XERNOX SHIELD Detects Malware Undetected for Over 5 Years
Bundled inside a GitHub auto‑clicker installer. The malware managed to evade detection for years. With zero detections in platforms such as VirusTotal (At the time of writing).
MR. XERNOX
12/21/20253 min read

Executive Summary
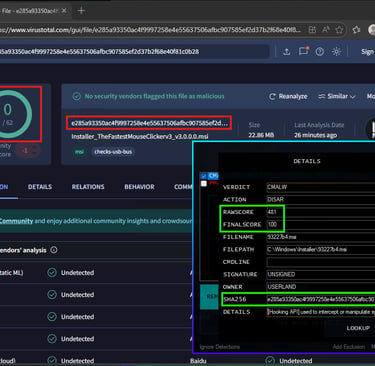
XERNOX SHIELD recently detected and neutralized a malicious payload that has remained fully undetected on VirusTotal for over five years. At the time of analysis, the sample still shows 0/70 detections across all major antivirus engines.
VirusTotal Scan Link: https://www.virustotal.com/gui/file/e285a93350ac4f9997258e4e55637506afbc907585ef2d37b2f68e40f81c0b28/detection
The malware was bundled inside an auto‑clicker installer distributed via GitHub, disguising itself as a harmless utility while exhibiting multiple high‑risk behaviors typically associated with advanced malware and destructive threats.
This detection was achieved without signatures, cloud reputation, or prior intelligence — relying solely on XERNOX SHIELD’s behavior‑first detection engine.
The Threat Context
Auto‑clickers are a common malware delivery vehicle because they:
Are frequently downloaded by users
Often run with elevated privileges
Are commonly distributed as unsigned installers
Receive less scrutiny from traditional AV engines
This particular installer abused that trust.
Despite being publicly available for years, the payload:
Was unsigned
Executed entirely in userland
Leveraged multiple evasion and interception techniques
Remained invisible to traditional detection models

VirusTotal Results
At the time of writing:
VirusTotal detections: 0 / 70 (still undetected)
File type: MSI installer (TheFastestMouseClicker v3.0.0)
Distribution: Public GitHub repository
Community score: Negative, but not malicious
Even after public analysis and disclosure, no security vendor on VirusTotal has flagged this file as malicious.
This stark contrast — 0/70 on VirusTotal vs. immediate detection by XERNOX SHIELD — highlights the limits of reputation-based security models.


What XERNOX SHIELD Saw
XERNOX SHIELD did not rely on file reputation or known signatures. Instead, it evaluated what the binary was capable of doing.
The following behaviors were identified during static and behavioral analysis:
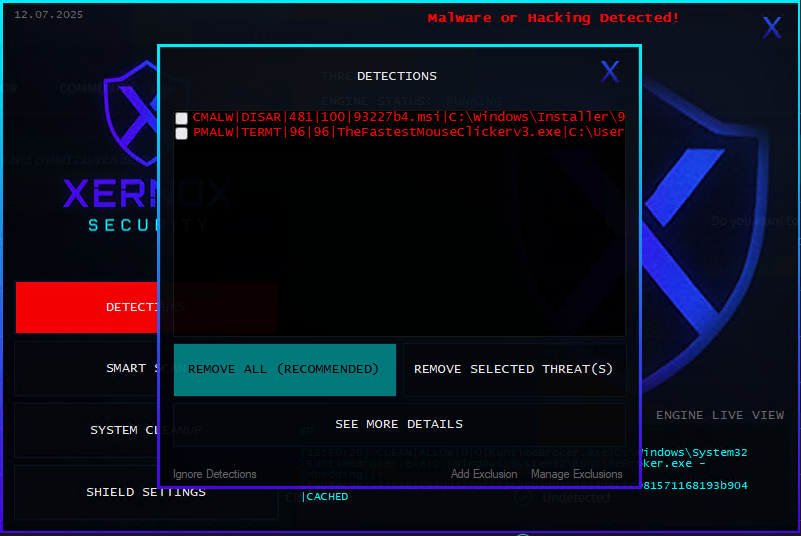
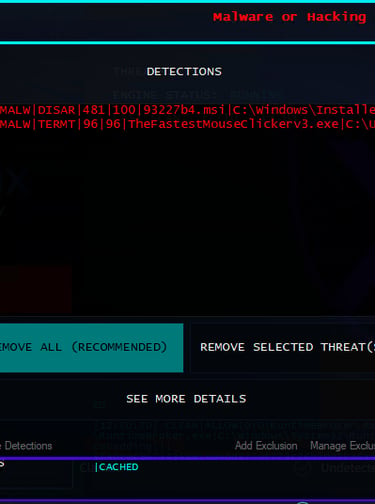
Dropper
TheFastestMouseClickerv3.exe -> C:\Windows\Installer\93227b4.msi
Interception & Hooking
Hooking APIs used to intercept or manipulate system events (multiple occurrences)
Obfuscation & Evasion
Runtime API resolution to evade static detection
Dynamic DLL loading via LoadLibraryA and LoadLibraryW
Anti‑debugging techniques: IsDebuggerPresent, CheckRemoteDebuggerPresent
Memory & Injection Capabilities
VirtualAlloc used to allocate executable memory
Remote process handle acquisition (OpenProcess)
Injection‑support primitives commonly seen in loaders
Disk & Low‑Level System Interaction
DeviceIoControl used on disk devices
SetFilePointer patterns consistent with sector‑level access
WriteFile used on raw handles
These behaviors strongly resemble techniques used in boot‑sector tampering, destructive malware, and stealth persistence mechanisms.
Trust & Identity Red Flags
Unsigned binary
Executed as a userland installer
Flagged as Potentially Unwanted Application (PUA) due to delivery method and trust violations
New Findings: Hidden Cryptocurrency Miner
Further independent analysis has now confirmed the true nature of this threat.
A full technical breakdown was published by Eric Parker on YouTube, revealing that the payload is a stealth cryptocurrency miner hidden inside the installer. The miner operates quietly, prioritizing persistence, evasion, and low system noise to remain unnoticed for long periods of time.
Despite this public analysis and confirmation of malicious intent:
VirusTotal still reports 0 / 70 detections
No major antivirus engine has classified the file as malicious
The sample remains widely misclassified as clean or benign
This validates XERNOX SHIELD’s original assessment and highlights a critical industry gap: malware that focuses on stealth and longevity can evade traditional detection indefinitely.
Final Thoughts
This was not a false positive. Not a heuristic guess. Not a reputation anomaly.
It was a real-world, long-lived, stealth coin miner that evaded the entire antivirus ecosystem for years.
XERNOX SHIELD detected it before public disclosure, without signatures, and without cloud intelligence.
That is the power of behavior-first detection.
If malware relies on being unknown — or on being ignored — it won’t survive XERNOX SHIELD.
Contact
Secure your digital world with us.
© 2025. XERNOX SECURITY LLC, All rights reserved.